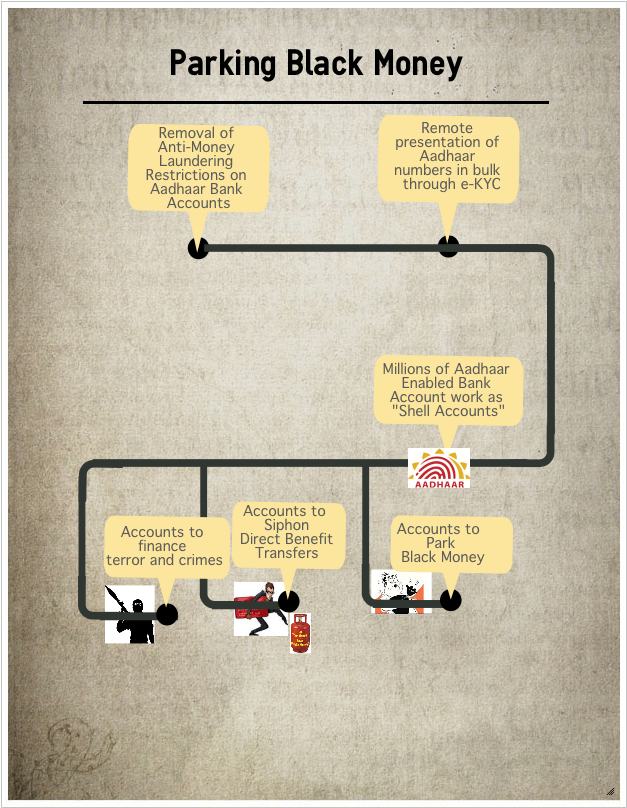
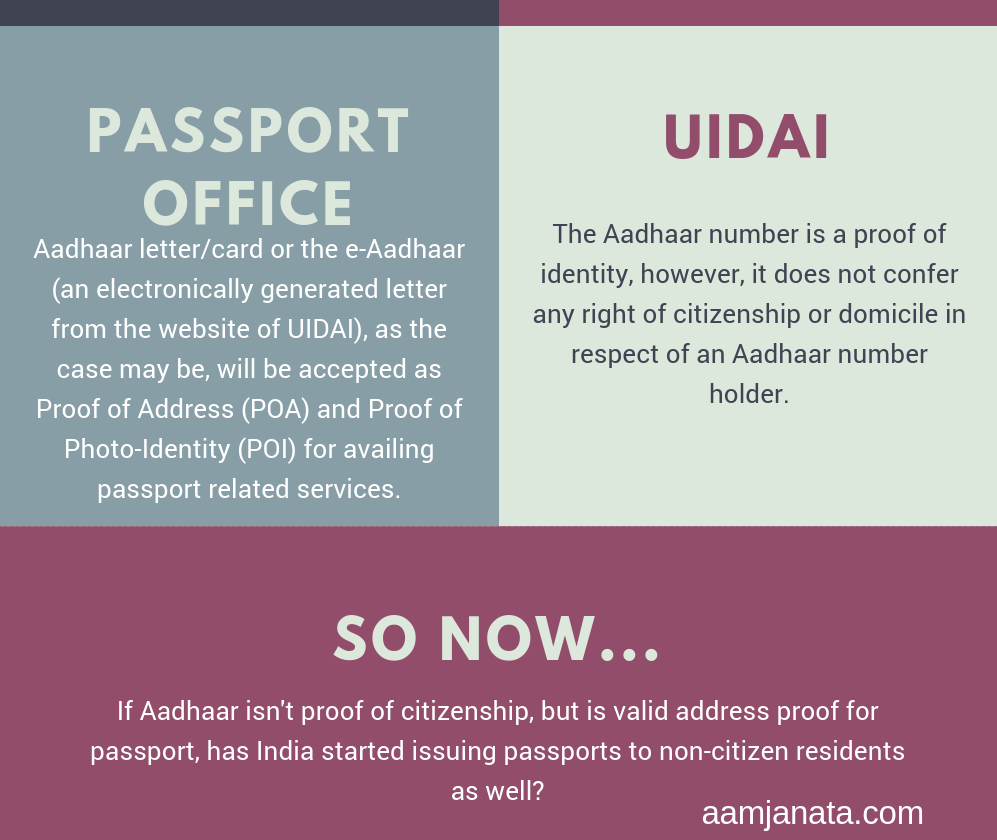
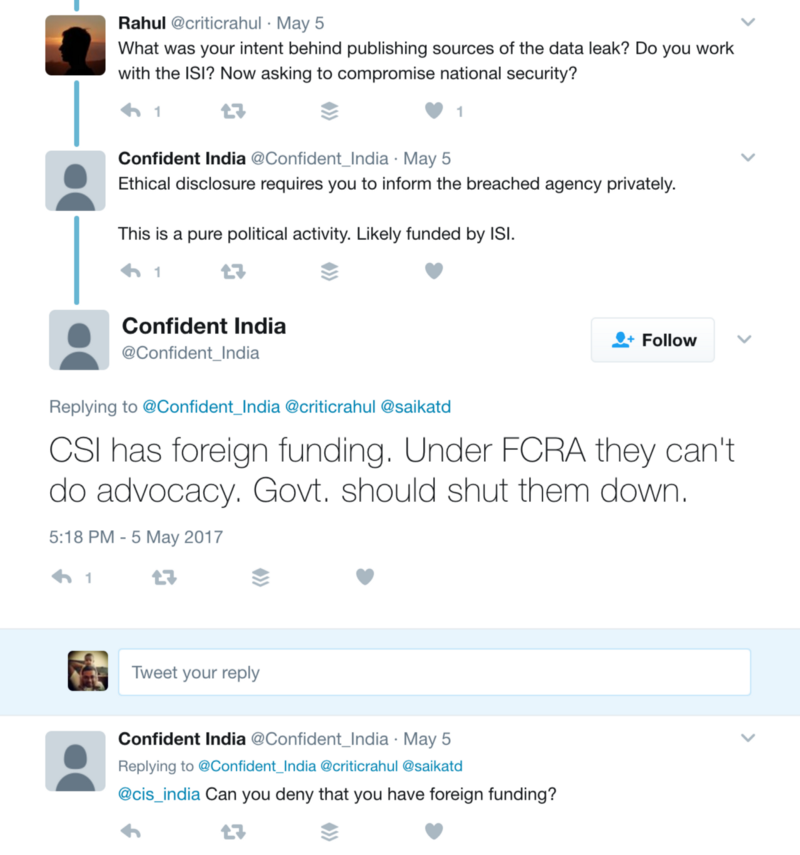
Farmers Protest: Is the opposition favoring middlemen?
In September 2020, Prime Minister Narendra Modi claimed that the opposition favored middlemen and hence opposed the farm laws that would benefit the farmers. This claim, as with anything Modi […]
Farmers Protest: Is the opposition favoring middlemen? Read More »