The government of India doesn’t seem to be interested in getting security vulnerabilities fixed. A CS engineer, Bhavyanshu Parasher, has been spending his time understanding the current security standards deployed by the government of India in most of its data-critical apps and websites. Last year, in September, he disclosed a security flaw in Prime Minster Narendra Modi’s web API that exposed user identifiable information like e-mail addresses and also that there was no proper authentication check for API endpoints. During that disclosure, he faced challenges because it was difficult for him to get in touch with concerned authorities. He mentioned on his blog that e-mail address mentioned on Google’s Play Store were not working. We had to contact @buzzindelhi (the handle used by BJP’s Arvind Gupta on Twitter) to help him get in touch with the concerned authorities.
“The e-mail address provided on Google’s Play Store returned a response stating “The email account that you tried to reach is over quota”. Had to get in touch with authorities via Twitter.”
Now, the same thing is happening again. He wants to disclose vulnerabilities in two major applications deployed by the Government of India but he is struggling to get in touch with the concerned authorities. He has published a post on his blog about it though he has not mentioned the specifics of the vulnerabilities yet, as he is hoping the government will patch them before he discloses them. However, this may be rendered moot, as our searches showed that at least one of the vulnerabilities has already been publicly disclosed, but not by Bhavyanshu. That security flaw is in an unpatched version of server software and there is a CVE assigned to it. Fix has been rolled out but developers are not aware of any of this. But then why wouldn’t it be so? UIDAI website still uses SSLv2 and SHA1 encoding in a world where SSLv2 has been phased out for over a decade now, and even free SSL certificates like the one used on this site come with SHA2 encoding because SHA1 isn’t considered secure. You can go to the UIDAI website and check this for yourself in your browser details for the SSL certificate.
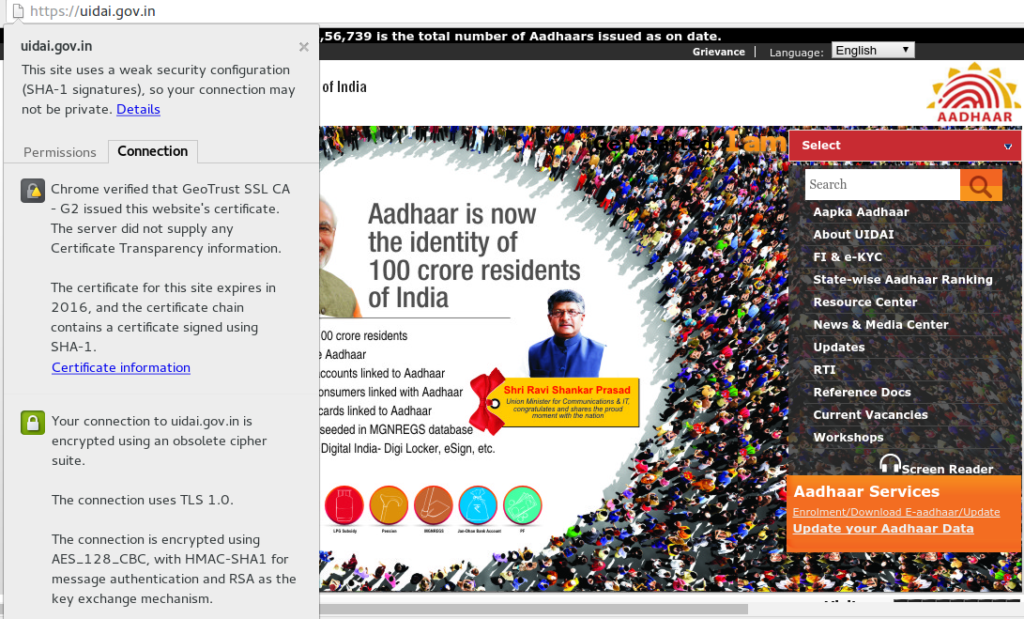
Bhavyanshu sent emails on March 24 and then again on April 4, but he hasn’t received any response. This time @buzzindelhi isn’t showing much enthusiasm in getting the vulnerabilities fixed either. In response he just directed him to the public Twitter handle of Akhilesh Mishra (Director, myGov). Hardly an acceptable process for initiating discussion about security breaches!
https://twitter.com/
One would expect Mr. Mishra to contact Bhavyanshu immediately, but the truth is that even he isn’t interested.There is, as yet, no reply from him.
It is cases like these which make the whole concept of Digital India look ugly. There are no dedicated e-mail addresses for security response teams. Official e-mail addresses don’t work and the apps are poor on security. It is a goldmine for unethical hackers and a complete deterrent for ethical hackers who would like to help the government fix security leaks. There is no way for the researchers to get in touch with the concerned authorities. A concept like Digital India, without guaranteed user data security and user privacy, should not be promoted by the Government of India as it puts many people at risk.
Considering the complete lack of interest in securing the vulnerabilities, we cannot provide too many details. However, people looking to exploit government data would already have found these and would be using them by now. This isn’t exactly rocket science. What data is vulnerable? Let us just say that I have seen e-mail addresses, Aadhaar numbers (where provided) and street addresses and can confidently say that a malicious hacker could write a script that replicates the data for all profiles. And before you think that such things are not done, just today, Madhu Menon posted a link to the hacked and leaked Turkish citizenship database.
Turkish Citizenship database dump. http://185.100.87.84/
Remember, tomorrow this could be Aadhar. @sunil_abraham
— Madhu Menon (@madmanweb) April 4, 2016
A similar database of MyGov.in users could prove devastating to BJP, given that their supporters are disproportionately more likely to have signed up. And while Bhavyanshu stresses that he would not do it, it isn’t outside the realm of belief that more malicious hackers not just could, but definitely would. And there seems to be no way to prevent this short of raising a public stink, because a government that claims to be interested in a Digital India does not seem to have the foggiest on digital security and the need to have developer teams rapidly rolling out fixes in the event vulnerabilities are found.
“Seems like the government doesn’t have dedicated security team for projects that need immediate attention to security flaws. Instead, people who wish to disclose vulnerabilities have to rely on Twitter handles to get in touch with them. I am doing a lot of volunteer work like this because I like the concept of Digital India but I don’t want it without data security and privacy. I have written a web app that will help eliminate this communication gap between researchers and authorities but whom to contact? Who are the concerned authorities after all? Don’t give me another Twitter handle!” , Bhavyanshu told me when asked about the current status of vulnerability disclosure. He also pointed us to privacy policy of MyGov and why people should push government for better data security.
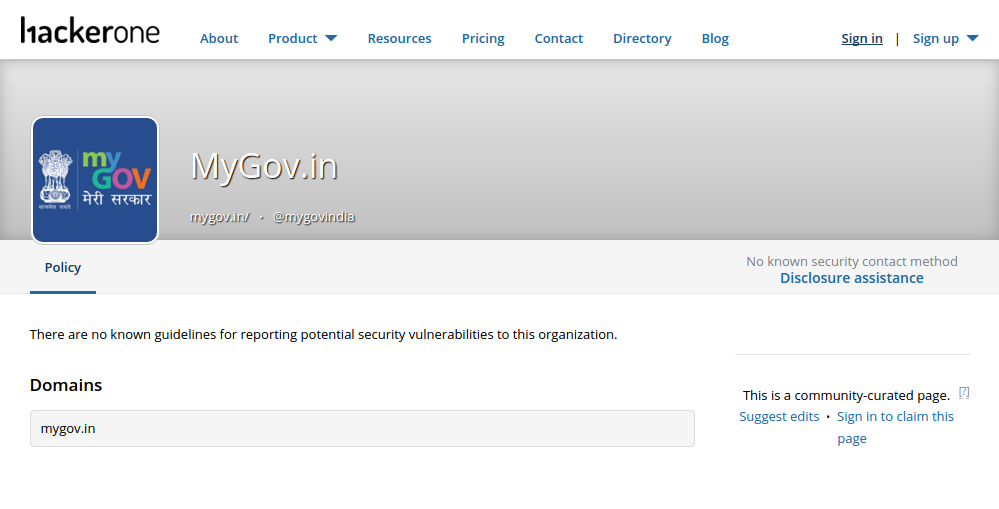
The page for MyGov.in on HackerOne – a bug bounty program by security leaders of top internet companies like Facebook, Microsoft and Google (that rewards hackers for finding and reporting vulnerabilities so that they can be fixed) says it all “There are no known guidelines for reporting potential security vulnerabilities to this organization.” Even the fact that the app has no known process for reporting vulnerabilities is an immediate flag. It tells hackers that there is no one keeping an eye on it or worried about security. The most beginning programmer puts a working address on Google Play for contacting the developer. Yet, the official application of the largest democracy in the world fails to do it.
Contrast this with the Hack The Pentagon challenge that is actively rewarding hackers to break in and expose security vulnerabilities so that they can be fixed. This is the country where, a few days ago, our Prime Minister gave a speech at the nuclear summit on April Fool’s Day explaining the need to fight terrorists using 21st century technology with modern technology.
Terror has evolved. Terrorists are using 21st century technology. But our responses are rooted in the past: PM Modi #ModiInUS
— TIMES NOW (@TimesNow) April 1, 2016
Yet, his government seems supremely unconcerned about unauthorized access to confidential information. As the UK just saw, in a country that uses technology extensively, a security breach can be used as an attack vector, when hackers hack into the water supply and change the composition of chemicals put into the tap water. A more famous example to recall could be the Stuxnet worm that damaged Iran’s nuclear facilities. Yep. Code resulting in real time damage to equipment. We have, in the past seen that banks too can be hacked. We have seen that election equipment can be rigged. What will it take for us to wake up before our money, our vote, our voice and even our physical location is compromised?
It is completely insane to push for a Digital India and inaugurate three websites a month without having the requisite push to secure the data that will now be vulnerable to theft, or facilities to access. If Digital India must be, then it must be preceded by a culture of taking technology seriously or the whole country will inevitably suffer.
MyGov privacy policy claims to protect user identifiable information. Below are the excerpts from their policy page.
1. “MyGov do not sell or share any personally identifiable information volunteered on this site to any third party (public/private). Any information provided on MyGov will be protected from loss, misuse, unauthorized access or disclosure, alteration, or destruction. MyGov gather certain information about the User, such as Internet protocol (IP) address, domain name, browser type, operating system, the date and time of the visit and the pages visited. MyGov make no attempt to link these addresses with the identity of individuals visiting our site unless an attempt to damage MyGov has been detected.”
(https://mygov.in/simple-page/terms-conditions/) 2. “Please note that MyGov do not share any personally identifiable information volunteered on this site with any third party (public/private). Any information provided to this website will be protected from loss, misuse, unauthorized access, disclosure, alteration, or destruction.”
(https://mygov.in/mygov-faq/)
Turns out that like many other things, this privacy policy is a jumla as well.

Most of your articles since past 2 years, when you decided to become an AAPi, have been complaints about a heartless government and helpless citizens with no recourse. This is another one in the series.
When the government ministers are, for the first time, accessible on multiple channels – letters, email, twitter and Facebook, it is a laughable claim that some ‘expert’ who unearthed a ‘major security flaw’ is unable to reach people. I’m sure he has not tried, or if he has, they have looked into it and found it not a threat. If he expects govt to reply to every email, regardless of merit, sorry but that’s not how governments work – not in India, not in US, of which you are so enamoured. A factoid – of the 25,000 odd FIA requests (same as RTI), 21,000 have been rejected by the US govt this year alone.
Hope you can regain your perspective and constructive approach again, which would make it worthwhile for me to read you again. Till then, goodbye.
Hi, Please see my blog
Digital India: Views, opinions, and new proposals on various Technology & Social and Community affairs. http://wp.me/p1ZsI2-J5
Please contact info@cert-in.org.in. Check the Vulnerability Reporting section of Cert-in.org.in CERT – Indian Computer Emergency Response Team.