Yash K S is a software developer. In the last year or so, his interest in identification methods led to him discovering a vulnerability in online banking that can allow a malicious attacker to use attacks like Man in the Middle or Man in the Browser to steal money from bank accounts.
He published his findings on his website. Here is my interview with him. [Note: It has been edited from the original informal chat for coherence, but the content is unaltered in meaning.] Italics are my questions.
Can you explain briefly your background, so that my readers can understand the work you do?
I have diploma in CS after 10th, after that I joined Anti-virus company as C programmer. I am into building system products like Anti-virus, e-learning, Backup & Recover. Last 15 years I have built a lot of systems products for corporates.
How did you become interested in banking transactions?
Since I worked in anti-virus for couple of years, I continued to learn about security even though I was involved in building other products. I always knew banks are breakable. Zeus trojan, for example. The important trojan existed last 5 years for western banks, but not Indian banks, and Indian banks continued to say online banking is secure compared with banks in the West. Around 4 years ago, I was trying to build a product which solves a problem of identitifying on the internet and I did extensive study on how banks work, as I built the product. Around 2 years ago, I developed a personal interest in seeing how secure Indian banks are and started analyzing Indian banks for security.
What is the basis of that claim by Indian banks – that online banking is secure compared with banks in the West?
Indian banks thought online banking is secure, since they are using Mobile device as additional factor to add Payee before transactions. Indian banks believe mobile is secure and they are trying to use that as second secure channel. When users adds a payee on a PC, they send this information to Mobile with OTP (One Time Password). Citibank, ICICI Bank – both of them use this method. In the case of ICICI Bank, they even have an additional transaction password and grid numbers, which the user needs to enter by looking at back side of the debit card. In HSBC bank, they dont use the same methods of ICICI and Citibank, they distribute hardware OTP (One Time Password) device, where it generates random number for every one minute. They assume this will not allow fraud transactions to happen without user knowledge. I believe they are not providing enough security for consumers in our country.
Who would be liable if someone stole money using the vulnerability you discovered?
If anybody looses money in online, end users are liable for that loss not banks, unless user proves to the bank, this fraud has not happend because of negligence. Negligence means, user system does not have any malicious programs which stole credentials or user did not give out uder credentials via phishing mail or user has not logged in some system which is not secure. This is very difficult to prove. Almost impossible, even for technical users. It becomes a user problem, bank does not take responsibility.
So, the bank simply washes its hands off the loss instead of fixing it? Not their problem?
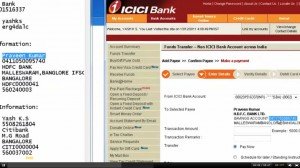
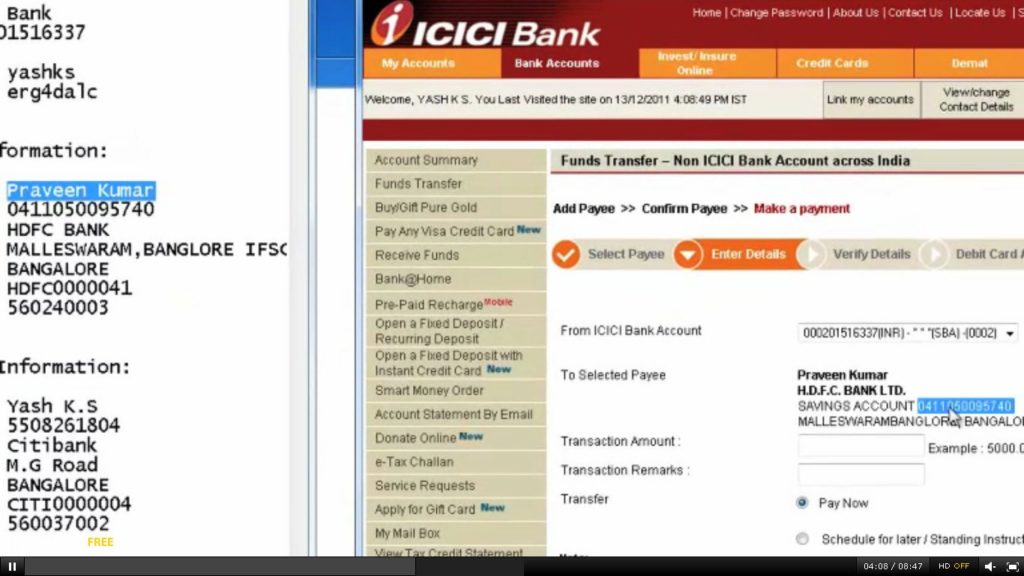
In my video what I have showed is – If a person is transferring money to Account 100, they see in their browser that the money is going to Account 100 and some X amount, but in back end malware changes data completly to Account 200 and some other amount. In this case, it is a Man in the Browser attack. The user is co-ordinating with malware without his own knowledge and the bank server fails to identify what is really happening in backend. Once the transfer of money is complete, if user sees the transaction via online, he still sees the same fake info, since the malware also knows to modify transaction statements.
Malwares are sophosticated and can fool both users and banks. Zeus trojan alone has costed 1 billion $ + loss in multiple banks in West. This trojan is still alive in wild and still causing losses. 5 years.
I built a similar trojan from scratch for Indian banks. Based on it, I have posted videos. I have not shared source code with anyone, keeping security in mind. I showed a few banks, in closed door meetings, this vulnerability. They were shocked to see it, but they have not fixed anything. One bank told, “Others banks might be insecure, but our bank is not”. After a month or so, I went back with trojan modified for this specific bank and showed them. They are back again in denial mode.
How is it that the same vulnerability works for all banks? Don’t all banks have their own systems – and methods?
The same trojan does not work for all banks. All banks have seperate systems, but if hacker companies writes the trojan using the concept of Man in browser and Man in middle, they can write specific malwares for each bank. Like I showed from my videos…. If I identified a security bug, banks can just fix the bug in the existing system. But, these problems are a system flaw, there is no way to fix it just by adding some stuffs. They need to replace the system itself by rethinking online banking security from the ground up.
So, you are saying, any bank account can be hacked? But can’t this misuse be traced?
Today hackers are not indivisuals, they operate as underground companies. They outsource work to each other based on the skill sets like we do in normal companies. It becomes very difficult to track it. In a chain, each are specialized in specific work, they complete the work, sell it and go.
What is the most important thing here?
There are important questions….. Who is responsible if users looses money via online due to trojans? Users keeps money in bank after a solid efforts, traditional method of banking have ensured always to make sure verify the person and dispatch the money. But, moment bank exposes money via internet for anyone who authenticates using username, password + additional stuffs, if a trojan can fool these factors, who becomes responsible? How can a user be responsibile? He likes convinenace, but he definitely does not want to loose money.
Do banks explain to all end users about the online threats and make them understand, before giving them an online account? Nope. It is the responsibility of the bank to provide a safe mechanism. An insecure web facility cannot be a user’s responsbility. When banks cannot give security for a specific types of attacks, they need to reduce the limit per day. They need to give insurance if they cannot solve the problem. They cannot make customer liable, since there is no way, anyone can expect a customer to know all about such threats.
Also make risks explicit, immediate transaction alerts, phone verifications?
Immediate transaction alerts exist today, due to RBI guidlines, there is no use. If a mobile has a malware which is co-ordinating with mobile trojan, then it will not even show an SMS for you.
How did banks respond to your information?
After the Citibank demo, within 2 weeks they changed system to add some information when they sent to mobile while adding payee. This mitigates a little. I appreciate Citibank for their quick reaction. But, if the same malware is expanded to mobile, complete online banking in india fails for all banks. Trojans (Zeus varients) already exists to peform co-ordinated attack by hijacking both PC and mobile of a user. There are many ways to infect both PC and Mobile, all smartphones connect to the internet or many smartphone users synch with PC. These two methods are enough to get a trojan into a mobile. Many more methods exist too. Android has more malwares compare to any other today.
ICICI Bank did not make any changes to security. Instead, they are posting on the internet saying what I am saying is wrong. After a month, they have sent a defamation case notice by asking me to pull down the content from my website. They have asked me to close my ICICI personal account too in a month.
HSBC, instead of solving problems, on 2nd Feb, people came to my house, after failed attempts to bring down content with the help of service providers. I was not present at that time; they asked my family members rude questions. I have registered an FIR. They were saying I am teaching how to hack HSBC! This is wrong! In my video, it only shows the consequences and how it is going to effect online banking customers.
Banks succeeded in removing my account from Vimeo.com. Vimeo deleted my account without informing me. After 5 months, instead of fixing problem. They are still trying to kill my content.
How many sites did your content get taken off from?
lol. Youtube, Bluthost.com, Dropbox, Vimdeo.com In ICDThost.com current hosting provided wanted me to remove direct links to video, although they were polite enough asking me, After that my site still survives there.
My intension of not pulling down the content is – This problem is not in one bank, ICICI bank thought I was targetting them alone, that was not true. But, all banks have the same issue, does not matter private or public banks today in india. I have showed this demo to RBI – Bangalore. They got a glimpse of what can happen to online transactions in country and they wanted me to proceed further to make more people within RBI aware of it, although we could not reach the executive chariman who handles payment settlements online.
So there are positive responses too.
Yes. there is a positive response too.
We had a discussion in national law school in Bangalore along with few experts, bankers, professor in that college itself. We have recorded that video. This DVD has given by professor of law school to cert-in personally. See this : Reserve Bank of India (RBI) : Man-in-browser attack – Top 100 banks of the world are reported to have experienced similar incidents – even RBI is saying last year itself. Banks are not lisetning to RBI either
Basically, we need to get support from RBI, Customers and pressure Banks for better security. That is the key.

can u paste the link of ur video here ..